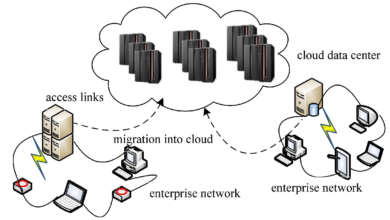
Compliance with Data Server Regulations
In today’s digital landscape, organizations face increasing pressure to comply with data server regulations to safeguard sensitive information and protect user privacy. With the rise in cyber threats and data breaches, it has become imperative for businesses to establish robust security measures and adhere to regulatory frameworks. This blog article explores the importance of compliance with data server regulations, providing a comprehensive understanding of the subject.
First and foremost, understanding the landscape of data server regulations is crucial. This article will delve into various regulatory frameworks such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Payment Card Industry Data Security Standard (PCI DSS). By familiarizing yourself with these regulations, you can ensure your organization’s compliance and avoid hefty fines or reputational damage.
The Significance of Data Server Compliance
Ensuring compliance with data server regulations holds significant importance for businesses of all sizes. Non-compliance can have grave consequences, including financial penalties, legal implications, and severe damage to an organization’s reputation. By complying with these regulations, organizations can enhance customer trust, strengthen data security, and foster a culture of privacy.
Protecting Sensitive Information
Compliance with data server regulations is crucial for protecting sensitive information such as personally identifiable information (PII), financial records, and healthcare data. By implementing appropriate security measures, organizations minimize the risk of unauthorized access, data breaches, and identity theft.
Reinforcing Customer Trust
Data server compliance plays a vital role in reinforcing customer trust. When individuals entrust their personal information to an organization, they expect it to be handled with care and in compliance with relevant regulations. By demonstrating compliance, organizations assure customers that their data is being protected and their privacy respected.
Avoiding Financial Penalties
Non-compliance with data server regulations can result in severe financial penalties. Regulatory bodies have the authority to impose fines based on the severity of the violation and the organization’s level of negligence. By adhering to these regulations, organizations can avoid the financial burden associated with non-compliance.
Mitigating Legal Risks
Compliance with data server regulations helps organizations mitigate legal risks. Failure to comply with these regulations may lead to legal action from affected individuals, regulatory bodies, or other stakeholders. By ensuring compliance, organizations minimize the risk of legal proceedings and associated costs.
Preserving Reputational Integrity
Reputation is paramount in today’s competitive business landscape. Non-compliance with data server regulations can severely damage an organization’s reputation, leading to loss of customers, partners, and business opportunities. By prioritizing compliance, organizations protect their reputational integrity and maintain a positive image in the eyes of stakeholders.
Understanding Key Data Server Regulations
To achieve compliance with data server regulations, organizations must have a solid understanding of the key regulatory frameworks that apply to their operations. This section provides an overview of some prominent data server regulations that organizations need to be aware of.
The General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) is a regulatory framework that applies to organizations handling the personal data of individuals within the European Union (EU). It sets forth strict requirements regarding data protection, consent, data subject rights, and breach notification. Organizations that process EU citizens’ personal data must ensure compliance with GDPR to avoid significant penalties.
California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA) is a state-level data privacy law that grants California residents certain rights over their personal information. It obligates businesses to disclose the categories of personal information collected, allow consumers to opt-out of the sale of their data, and provide mechanisms for data deletion. Organizations that collect personal information from California residents must comply with CCPA.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a globally recognized security standard that applies to organizations that handle credit card information. PCI DSS aims to protect cardholder data by implementing stringent security controls, including encryption, access controls, and network monitoring. Compliance with PCI DSS is mandatory for organizations involved in payment card transactions.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA) is a US federal law that sets standards for the protection of individuals’ medical records and other personal health information. HIPAA applies to healthcare providers, health plans, and other entities handling protected health information (PHI). Compliance with HIPAA ensures the privacy and security of sensitive healthcare data.
Gramm-Leach-Bliley Act (GLBA)
The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Modernization Act, applies to financial institutions such as banks, credit unions, and insurance companies. It requires these institutions to implement safeguards to protect customers’ non-public personal information. Compliance with GLBA ensures the security and confidentiality of financial data.
Implementing Data Encryption and Access Controls
Data encryption and access controls are essential components of data server compliance. This section explores the importance of encrypting sensitive data and implementing stringent access controls to protect against unauthorized access and data breaches.
Symmetric and Asymmetric Encryption
Data encryption involves converting plain text into a coded format to prevent unauthorized access. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses a pair of keys, namely a public key and a private key. Implementing encryption ensures the confidentiality and integrity of sensitive data.
Secure Access Controls
Access controls play a crucial role in data server compliance. Organizations should implement robust access control mechanisms, including strong passwords, multi-factor authentication (MFA), and role-based access control (RBAC). These measures ensure that only authorized individuals can access sensitive data and perform specific actions based on their roles and responsibilities.
Implementing Data Loss Prevention (DLP) Solutions
Data Loss Prevention (DLP) solutions help organizations prevent the unauthorized transmission or storage of sensitive data. These solutions monitor and control data in motion, at rest, and in use, ensuring compliance with data server regulations. By implementing DLP solutions, organizations can detect and prevent data breaches and unauthorized data transfers.
Securing Remote Access
With an increasing number of employees working remotely, securing remote access to data servers is vital for compliance. Organizations should establish secure virtual private network (VPN) connections, enforce strong authentication protocols, and regularly monitor and audit remote access activities to prevent unauthorized access and data exfiltration.
Regularly Patching and Updating Systems
Regularly patching and updating systems is crucial for data server compliance. Organizations should promptly apply security patches and updates to operating systems, applications, and devices to address known vulnerabilities. Failure to do so may expose systems to potential exploits and compromise data security.
Data Retention and Destruction Policies
Establishing effective data retention and destruction policies is essential for data server compliance. This section explores best practices for defining retention periods, ensuring secure storage, and implementing proper data disposal methods to mitigate the risk of unauthorized access and data breaches.
Defining Retention Periods
Organizations must define retention periods for different types of data based on legal requirements and business needs. Retention periods should consider factors such as the type of data, purpose of collection, and applicable regulatory frameworks. By clearly defining retention periods, organizations can manage data effectively and dispose of it when no longer necessary.
Secure Storage and Access Controls
Secure storage of data is crucial for data server compliance. Organizations should implement measures such as encrypted storage, secure file transfer protocols, and access controls to prevent unauthorized access. By limiting access to authorized personnel and regularly monitoring data storage infrastructure, organizations can minimize the risk of data breaches.
Secure Data Disposal Methods
Data server compliance requires organizations to implement proper data disposal methods to ensure that sensitive information is irreversibly destroyed. Secure data disposal methods may include physical destruction of storage media, degaussing, or secure data wiping using certified software. By following proper disposal procedures, organizations can prevent data leakage and comply with regulatory requirements.
Documenting Data Retention and Disposal Processes
Documenting data retention and disposal processes is essential for data server compliance. By maintaining records of retention periods, data storage locations, and disposal methods, organizations can demonstrate their commitment to compliance. Detailed documentation also facilitates audits and compliance reviews by regulatory bodies.
Conducting Regular Vulnerability Assessments
Proactively assessing vulnerabilities is crucial for data server compliance. This section emphasizes the significance of identifying and addressing security weaknesses promptly to prevent data breaches and ensure compliance with regulatory requirements.
Vulnerability Scans and Penetration Testing
Regular vulnerability scans and penetration testing help organizations identify and remediate security vulnerabilities. Vulnerability scans involve automated tools that scan networks, systems, and applications for known vulnerabilities. Penetration testing goes a step further by simulating real-world attacks to identify weaknesses that may not be detected by automated scans.
Security Audits and Compliance Assessments
Regular security audits and compliance assessments play a vital role in data server compliance. These processes involveevaluating an organization’s security controls, policies, and procedures to ensure they align with regulatory requirements. Through security audits and compliance assessments, organizations can identify areas of improvement and take appropriate measures to address any gaps in their data server security.
Addressing Vulnerabilities and Patching
Once vulnerabilities are identified through vulnerability assessments, organizations must take prompt action to address them. This involves patching systems, updating software, and implementing necessary security measures to mitigate the risk of exploitation. Regularly patching systems ensures that known vulnerabilities are patched, reducing the potential for data breaches.
Implementing Intrusion Detection and Prevention Systems
Intrusion detection and prevention systems (IDPS) are essential tools for data server compliance. IDPS monitor network traffic and detect suspicious activities or potential intrusions. By implementing IDPS, organizations can quickly identify and respond to potential security breaches, preventing unauthorized access to sensitive data.
Regular Security Awareness Training
Security awareness training is a critical aspect of data server compliance. Employees play a significant role in maintaining data security, and training them on best practices, such as identifying phishing attempts, using strong passwords, and reporting suspicious activities, helps create a culture of security within the organization.
Third-Party Security Assessments
Engaging third-party security assessors can provide an unbiased evaluation of an organization’s data server security. These assessments can help identify potential vulnerabilities, assess compliance with regulatory requirements, and provide recommendations for improvement. Third-party assessments add an extra layer of assurance and demonstrate an organization’s commitment to compliance.
Ngadsen test2
Employee Training and Awareness
Ensuring compliance with data server regulations requires the active participation of employees. This section focuses on the importance of providing comprehensive training programs to educate employees about data security best practices, privacy guidelines, and regulatory requirements. By promoting a culture of awareness, organizations can minimize the risk of internal data breaches.
Creating a Security Awareness Program
Organizations should develop a comprehensive security awareness program to educate employees about the importance of data security and compliance. This program should cover topics such as identifying phishing attempts, secure password practices, handling sensitive data, and reporting security incidents. Regular training sessions and awareness campaigns help reinforce security practices and keep employees informed about evolving threats.
Role-Based Training
Employees have different roles and responsibilities within an organization, and their training needs may vary. Role-based training ensures that employees receive training tailored to their specific job functions. For example, IT staff may require more technical training on secure coding practices, while non-technical employees may benefit from general security awareness training.
Continuous Training and Updates
Data server regulations and security threats are constantly evolving. Therefore, continuous training and updates are essential to keep employees informed about the latest best practices and regulatory changes. Regularly scheduled training sessions, newsletters, and security bulletins can help employees stay up to date and adapt their practices accordingly.
Simulated Phishing Exercises
Simulated phishing exercises can be an effective way to assess employees’ susceptibility to phishing attacks and raise awareness about the risks associated with social engineering. By conducting these exercises, organizations can identify areas of improvement and provide targeted training to mitigate the risk of successful phishing attempts.
Employee Accountability and Reporting
Employees should be encouraged to take ownership of data security and report any suspicious activities or potential security incidents promptly. Establishing clear reporting channels and promoting a culture of accountability ensures that potential threats are addressed in a timely manner, reducing the impact of data breaches and facilitating compliance with data server regulations.
Incident Response and Breach Notification
In this section, we delve into the key elements of an effective incident response plan. We discuss the importance of promptly detecting and responding to security incidents, as well as the obligation to report breaches to the relevant authorities and affected individuals. Understanding breach notification requirements is crucial for data server compliance.
Developing an Incident Response Plan
An incident response plan outlines the steps to be taken in the event of a security incident. It includes procedures for incident detection, containment, eradication, and recovery. Developing a well-defined incident response plan ensures that organizations can respond effectively to security incidents, minimize the impact, and maintain compliance with data server regulations.
Establishing an Incident Response Team
An incident response team comprises individuals with specific roles and responsibilities in managing security incidents. This team may include representatives from IT, legal, communication, and management departments. By establishing a dedicated incident response team, organizations can ensure a coordinated and timely response to security incidents.
Implementing Incident Detection and Monitoring Systems
Implementing robust incident detection and monitoring systems is crucial for prompt incident response. Intrusion detection systems (IDS), security information and event management (SIEM) solutions, and log analysis tools help monitor network traffic, detect anomalies, and identify potential security incidents. By leveraging these systems, organizations can detect and respond to incidents in a timely manner.
Breach Notification Obligations
Regulatory frameworks often require organizations to notify affected individuals and relevant authorities in the event of a data breach. Organizations must have a clear understanding of breach notification obligations, including the timelines and specific information to be included in the notifications. Prompt and transparent breach notification is essential for maintaining compliance with data server regulations.
Communicating with Affected Individuals
When a data breach occurs, organizations must communicate with affected individuals to inform them about the breach, the potential impact, and the steps they can take to protect themselves. Clear and concise communication is crucial to maintaining trust and complying with regulatory requirements. Organizations should provide guidance on actions such as changing passwords or monitoring financial transactions.
Cloud Computing and Data Server Compliance
Cloud computing has revolutionized the way organizations store and process data. This section explores the implications of utilizing cloud services in terms of data server compliance. We discuss the shared responsibility model, data sovereignty considerations, and the importance of selecting cloud providers with robust security measures and regulatory compliance certifications.
The Shared Responsibility Model
Cloud service providers typically operate on a shared responsibility model, where they take responsibility for certain aspects of data security, while the customer remains responsible for others. Organizations must understand the division of responsibilities outlined in the cloud service provider’s terms and conditions. This understanding helps ensure compliance with data server regulations.
Data Sovereignty and Cross-Border Data Transfers
Data sovereignty refers to the concept that data is subject to the laws and regulations of the country in which it is located. When utilizing cloud services, organizations must consider the implications of cross-border data transfers and ensure compliance with applicable data protection and privacy laws. Understanding data sovereignty helps organizations maintain compliance and protect the privacy of their data.
Selecting a Secure Cloud Provider
Choosing a cloud provider with robust security measures and regulatory compliance certifications is essential for data server compliance. Organizations should evaluate the provider’s security standards, certifications such as ISO 27001 or SOC 2, and data protection mechanisms. A thorough assessment of the cloud provider’s security practices ensures that data remains secure and compliant in the cloud environment.
Performing Due Diligence and Contractual Agreements
Prior to engaging a cloud service provider, organizations should perform due diligence to assess the provider’s capabilities and commitment to data security. This involves reviewing security documentation, conducting audits or assessments, and negotiating contractual agreements that clearly outline data security obligations. Adequate due diligence and contractual agreements help organizations maintain control over their data and ensure compliance.
Auditing and Monitoring Data Server Activities
Regular auditing and monitoring of data server activities are essential for maintaining compliance. This section highlights the significance of implementing logging mechanisms, analyzing logs for suspicious activities, and conducting periodic audits to ensure adherence to regulatory requirements. We also touch on the importance of implementing intrusion detection and prevention systems.
Implementing Logging and Log Analysis
Implementing logging mechanisms is essential for auditing and monitoring data server activities. Logs capture important information such as user actions, system events, and security incidents. By analyzing logs, organizations can detect anomalies, identify potential security breaches, and demonstrate compliance with data server regulations. Log analysis tools help automate the process of reviewing and correlating logs for potential security incidents.
Conducting Regular Audits and Assessments
Regular audits and assessments of data server activities provide valuable insights into an organization’s security posture and compliance status. Internal or external auditors can evaluate security controls, assess adherence to policies and procedures, and identify areas for improvement. Regular audits help organizations maintain compliance, demonstrate due diligence, and continually enhance their data server security.
Intrusion Detection and Prevention Systems
Intrusion detection and prevention systems (IDPS) play a crucial role in monitoring data server activities and detecting potential security incidents. These systems analyze network traffic, identify patterns that indicate malicious activities, and trigger alerts or automated responses. By implementing IDPS, organizations can detect and respond to security incidents in real-time, minimizing the impact on data security and compliance.
Implementing Continuous Monitoring
Continuous monitoring ensures that data server activities are consistently monitored for potential security incidents. This involves real-time analysis of logs, network traffic, and system events to detect anomalies or suspicious activities. By implementing continuous monitoring practices, organizations can identify potential security breaches promptly, respond effectively, and maintain compliance with data server regulations.
St
Staying Ahead of Evolving Data Server Regulations
Data server regulations continue to evolve to address the changing threat landscape. This final section discusses the importance of staying updated with the latest regulatory developments. We explore resources such as industry forums, regulatory websites, and professional networks that can help organizations stay ahead and adapt their data server compliance strategies accordingly.
Industry Forums and Associations
Industry forums and associations provide valuable platforms for staying updated on the latest data server regulations. Participating in relevant industry forums allows organizations to engage in discussions, share experiences, and gain insights from peers and experts. These forums often provide information on upcoming regulatory changes, best practices, and compliance strategies.
Regulatory Websites and Resources
Regulatory bodies maintain websites that serve as authoritative sources of information on data server regulations. Monitoring these websites helps organizations stay informed about new regulations, amendments, and enforcement actions. Regulatory websites often provide guidance documents, FAQs, and resources that assist organizations in understanding and complying with the applicable regulations.
Professional Networks and Conferences
Professional networks and conferences offer opportunities to connect with industry professionals, attend educational sessions, and gain insights into emerging trends and best practices in data server compliance. Engaging with professionals in the field and attending relevant conferences keeps organizations informed about regulatory developments and fosters a culture of continuous learning.
Engaging Legal and Compliance Experts
Engaging legal and compliance experts can provide organizations with specialized knowledge and guidance on data server regulations. These experts stay up to date with the regulatory landscape and can help organizations interpret complex requirements, assess compliance readiness, and navigate regulatory challenges. Legal and compliance professionals can provide valuable advice on implementing effective compliance strategies.
Conducting Regular Compliance Assessments
Regularly assessing compliance with data server regulations is crucial to ensure ongoing adherence. Organizations should conduct periodic internal assessments or engage external auditors to evaluate their compliance status. These assessments help identify any gaps or areas for improvement, allowing organizations to take corrective actions and maintain compliance with evolving regulations.
In conclusion, compliance with data server regulations is essential for organizations seeking to protect sensitive information, maintain customer trust, and avoid legal and financial repercussions. By understanding the landscape of data server regulations, implementing robust security measures, fostering a culture of compliance, and staying updated with the latest regulatory developments, businesses can effectively safeguard their data and ensure privacy in the digital age. Through a proactive approach to compliance, organizations can not only meet regulatory requirements but also enhance their overall data security posture.